In the age of digitalization, IT security is essential for companies to combat cybercrime. Attacks on IT systems are becoming increasingly common and can cause vast damage. Our IT security consultancy and modern security solutions can help you to protect your business against attacks and minimize security risks.
IT security consulting: comprehensive IT security services for companies
IT security: advice and solutions for companies
Our IT security consultancy and solutions provide comprehensive protection. We can develop IT security management concepts tailored to your needs, lay the necessary technical foundations and offer both offensive and defensive services. We’ll constantly review your current IT security status and make sure you are prepared as effectively as possible for potential attacks before they happen. And, of course, we will be at your side to provide emergency assistance to repel any cyberattacks that do occur.
The only way to ensure effective, long-term information security is by systematically embedding these processes into an overarching management system. An information security management system (ISMS) enables companies to deploy available resources in a targeted manner, identify weaknesses at an early stage, assess risks and gain transparent insights into the success of security measures.
We design and implement information security management processes in line with established standards, thereby helping you to meet regulatory requirements and upgrade your security processes to a high level. At the same time, we always keep your specific requirements in mind.
Our core IT security management services:
Development of IT risk strategies, implementation of business impact analyses and support with implementation
Implementation and optimization of information security management systems, maturity analyses, preparatory work for certifications, and governance, risk and compliance solutions
Development of emergency handbooks, simulation of crisis situations and individual emergency process modeling
Support with implementation of industry-specific regulations, such as NIS2, the EU AI Act, KRITIS and TISAX
Creation and optimization of data protection concepts, implementation of data protection audits and acting as an external data protection officer
Preventative measures can identify many cyber threats at an early stage and even thwart them to a large extent, minimizing the risk to your company. A well-designed IT security architecture significantly reduces risk and ensures that sensitive data and critical systems are kept protected. Cyberattacks target various weaknesses – from security flaws in individual applications to compromising insufficiently secured encryption systems. We protect companies as effectively as possible by developing customized security solutions precisely tailored to your specific requirements.
Our core technical information security services:
Development of cloud security strategies, optimization of cloud configurations (such as Microsoft Azure and AWS), implementation of cloud security monitoring, network security solutions, extended detection and response (XDR), network detection and response (NDR) and mobile security
Establishment and optimization of public key infrastructures (PKIs), implementation of secure trust structures, credential management, consultancy on multi-factor authentication (MFA), zero trust models and post-quantum cryptography
Effective identity and access management (IAM) is essential for protecting sensitive company resources. We can advise you on privileged access management (PAM) and help implement safe and efficient access controls for your systems.
We support companies in establishing powerful defense capabilities and tools. Security information and event management (SIEM), security orchestration, automation and response (SOAR) and vulnerability management form the backbone of your defenses. We can also assist you with threat intelligence and help you to uncover advanced persistent threats (APTs).
Our security experts advise development teams on secure software development and review web applications for weaknesses. We implement single sign-on (SSO) and secure deployment pipelines. In addition, we ensure compliance with the Open Worldwide Application Security Project (OWASP) Top 10 security guidelines.
Attacks are increasingly targeting networked systems in industrial companies. We analyze risks in operational technology (OT) and implement tailored security solutions to protect industrial control systems and IoT devices. In addition, we conduct supply chain security assessments to minimize weaknesses in production activities.
Given the current threat situation, purely defensive security strategies are not enough. By simulating cyberattacks, we can identify weaknesses in your IT infrastructure in a targeted manner – before real attackers can exploit them. You gain valuable insights into critical security flaws, potential damage and your company’s ability to withstand real-life threats. The results of our penetration tests enable you to make targeted optimizations to your IT security, strengthening your defenses to withstand different types of attack.
Our core offensive IT security services:
We conduct targeted analyses of applications and infrastructure in search of weaknesses before helping you to secure any identified security flaws.
Our specialists review your assets from an attacker’s perspective, using real cyberattack tools. We offer:
- Web application & API pentesting – Identification of security flaws in web applications and interfaces
- Infrastructure & cloud pentesting – Review of cloud environments and IT infrastructure for potential attack vectors
- Mobile pentesting (iOS/Android) – Targeted security analysis of mobile applications to identify weaknesses
- Rich internet application & fat client pentesting & reverse engineering – Analysis of complex applications and client-based software, searching for security flaws
- Embedded device & IoT pentesting – Ensuring that suitable security measures are in place for networked devices and embedded systems
- AI pentesting – Examination of security risks in AI-powered applications and systems
- SAP pentesting– Analysis of SAP environments to identify potential points of attack
Our team conducts highly realistic security simulations to test and optimize your defense mechanisms. This includes:
- Technical measures to improve IT security.
- Open source intelligence (OSINT) to identify publicly available information about your company.
- Social engineering to uncover human weaknesses in security processes.
- Physical security assessments to assess measures designed to protect physical assets.
- Resilience consultancy to help your IT security structure withstand attacks.
Effective protection against cyberattacks requires robust defensive security measures. Our team provides comprehensive defensive security services you can depend on to protect your IT infrastructure.
Our core defensive IT security services:
Configuration, monitoring and maintenance of firewalls to prevent unauthorized access
Ensuring controlled and secure network access control for both physical and cloud-based networks
Operation and optimization of network infrastructure for optimal availability and security
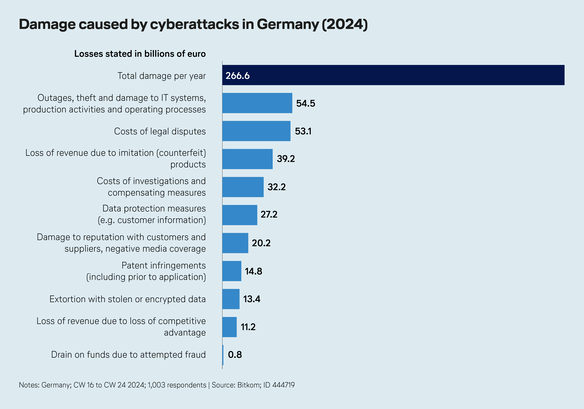
Cybersecurity in Germany: Attacks cause extensive damage
Every year, cyberattacks cause massive economic damage in Germany. Outages, theft and damage to IT systems, production activities and operating processes cause the most significant damage at €54.5 billion per year – with the automotive and logistics industries targeted in particular. Plagiarism and industrial espionage cause €39.2 billion of damage per year, with the high-tech and chemical industries particularly heavily affected. In addition, data protection breaches place a financial burden on companies, causing some €27.2 billion of damage per year. Blackmail with stolen data or encryption causes damage totaling €13.4 billion each year. Cybercriminals tend to focus their blackmail attempts on banks and financial institutions – though ransomware attacks on hospitals represent a growing threat, as these incidents can block essential patient data and bring life-saving processes to a standstill.
(Quelle: Bitkom; ID 444719)
Our IT security expertise
With decades of experience dealing with the stringent security requirements in the aerospace industry, Lufthansa Industry Solutions has extensive expertise in information security. We combine this experience with specialist knowledge of specific industries, which enables us to meet specific methodological requirements and fulfill company-specific security requirements as effectively as possible.
Are you interested in our IT security consultancy services and solutions?
Would you like to identify IT security flaws in your company? Maybe you’re looking for measures to improve your information security? We would be happy to advise you. Fill in our contact form to request a non-binding quotation – we look forward to hearing from you.